Web security vulnerabilities are on the rise as technology advances. Every day, around 30,000 websites are hacked. Everyone who is interested in reducing their website’s vulnerability should learn about and implement security principles. “It won’t happen to me” is a dangerous mindset. If you neglect online security issues, security breaches happen quickly, even though you may not have anticipated your website being hacked. As a result, you may simply assume that your site’s security is of the utmost importance.
Web security risks necessitate a proactive and protective approach. To that end, this blog aims to raise awareness of the importance of website security, the types of web malware that can invade your website, and how they can be protected.
Buck up and learn everything you can about how to keep your website safe.
What is website security? And why is it important?
Any action you take to keep your website safe from a cyberattack falls under the umbrella of website security. It includes cloud security and web application security, which protect cloud services and web-based applications, respectively. However, website security is never like a “set-it-and-forge-it” thing. It is an ongoing and never-ending process.
Web security is a must-have for any company that relies on computers and the internet. If hackers get into their systems or software or change it, websites and even whole networks can go down and business operations ought to stop.
Vulnerabilities & Threats to Web security and its solution:
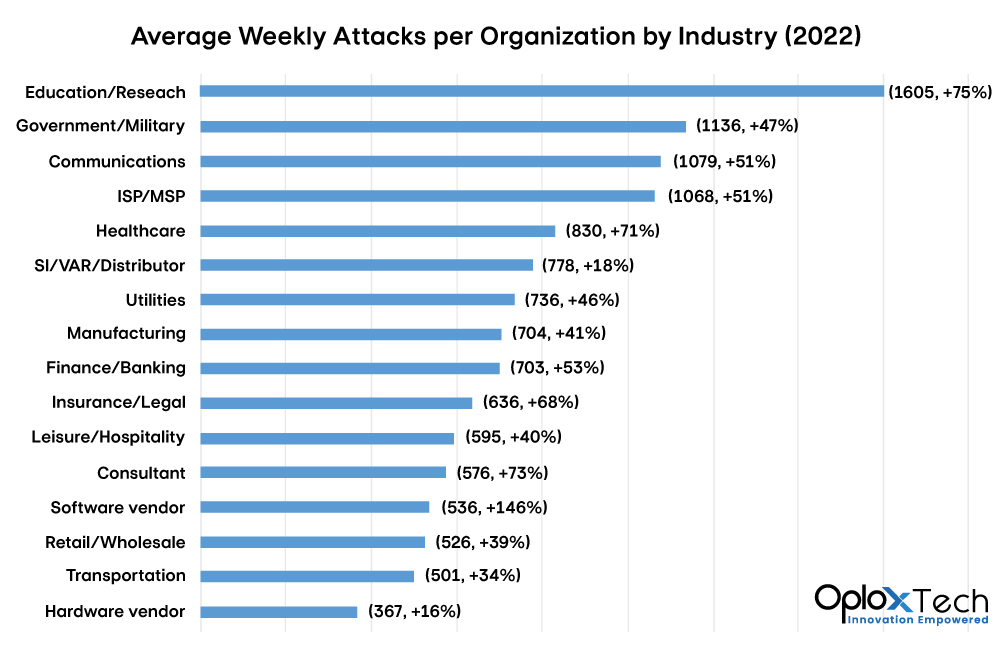
There are more risks and vulnerabilities to web security in 2022 than there were in 2021:
- There were about 47.5 million attacks in the U.S. in the first three months of 2021. During the same time period in 2022, that number rose to 51 million.
- In 2022, Some estimates say that more than 2,200 cyberattacks happen every day. About one cyberattack happens every 39 seconds.
- In 2021, ransomware damage and ransom payments cost more than $20 billion around the world. By 2031, this number is expected to reach more than $265 billion.
The main security risks to your website that you may not be aware of are as follows.
1-Injection Flaws: SQL, XSS, OS command Injections:

An injection flaw is a weakness that lets an attacker send malicious code from one system to another through an application. This can mean taking over both the back-end systems and other clients that are connected to the vulnerable application.
Some of the results of these threats are:
- letting a hacker make calls to the operating system on a target device
- letting a hacker get into backend database systems
- letting a hacker compromise or take over other users’ forums
- letting an attacker force other users or services to do things
Types of Injection flaws:
Following are the main three types of injection flaws:
I-SQL injection:
It is a common injection in which the hacker tricks the website by adding malicious code to the SQL query. A website sends these kinds of queries to the databases. Because of this, the returned database result will be based on the information the attacker wants instead of the information expected by the website.
Defence Options:
- Use character escaping in a proper manner.
- Utilize input validation, which is the proper testing of the data the user gives.
- Put in place a parametrized query that needs at least one parameter to run.
II-OS Command Injection:
Malicious parameters can modify a regular user’s file access system call to access another user’s file, so gaining access to that user’s data. To put it another way, a system command injection occurs when software creates an operating system command utilizing externally-influenced input but fails to properly neutralize specific aspects that can change the initial intent of a command.
Defence Options:
- Don’t directly call OS commands. Built-in library functions are an excellent substitute to OS Commands
- Use structured mechanisms that automatically keep data and commands separate.
- Each OS has its own set of escape values that are added to commands.
- Verify commands against the list of commands that are allowed. Define the length of characters, strings, and other regular expressions in a clear way.
III-Cross-Site Scripting (XSS):
Cross-site scripting attacks are carried out by injecting malicious client-side scripts into a website and exploiting the website as a propagation technique.
A hacker tries to break into your website by giving it JavaScript tags on input. If this input is given back to the user without being cleaned first, the user’s browser will run it. It can be as simple as making a link and getting someone to click on it, or it can be a lot worse. The script runs when the page loads and can, for example, be used to send your cookies to a hacker.
Defence Option:
- All of the data should be inspected before being put in.
- Use the least privileges to perform the function
- Don’t send HTML tags back to the user
IV-LDAP Injection:
LDAP Injection is a type of attack that takes advantage of websites that build LDAP statements based on what the user types in. When an application doesn’t properly filter user input, it’s possible to manipulate LDAP statements for the attackers.
An LDAP injection attack could allow access to illegal queries and modify data within the LDAP tree.
Defence Option:
- Use the suitable LDAP encoding function to escape all variables.
- Use Frameworks that Prevent LDAP Injection Automatically
- Reduce the level of access that the LDAP binding account has
- Validate Allow-List Input
These four injection attacks are the most frequent ones that might compromise website security. However, by using the above-mentioned security measures, website hacker manipulation can be avoided.
2-Broken authentication in web security:

Through authentication, the web application’s data and rights are only accessible by confirmed users. However, when the authentication is compromised, the hacker gets around the login security and has access to all of the user’s credentials.
Broken authentication can happen for a variety of reasons.
- Errors in session management could make it possible for sessions to be hijacked.
- a user session ID that appears in the website’s URL
- Poor password encryption leads to credential stuffing.
- Using the weakest password could result in password spraying.
- providing the user manipulated links that look like they were provided by the website
Defence Options:
The following are many options for preventing a website’s authentication from failing.
- To confirm the user’s identity, employ multi-factor authentication (MFA).
- Disallow weak passwords while forcing the user to set the password with a certain length and special character.
- Employ a cracked password protection method that locks user accounts until they replace the password.
- Passwords must be salted, hashed, and encrypted.
- Set a maximum number of user-login attempts from a specific IP address to prevent brute-force attacks.
In order to meet the ever-evolving global standards for cyber security, you must use strong cyber security systems to secure your company’s data and that of your customers.
3-Insecure direct object references (IDOR) in web security:

Using an ID for direct object access without extra authorization checks is another website security vulnerability known as IDOR. In order to evade the authentication process, a hacker only needs to change the values of parameters in a URL or in the password. Hence, successfully breached the ID
IDOR vulnerabilities in case of transaction:
For the most part, websites rely on database-generated IDs. The mechanism used to generate database keys is a pretty simple one: the next available integer is usually used. The same database ID generating procedures are applied to all other database records.
How is this approach the worst?
Suppose that the URL has the following transaction details of a user ID.
https://www.example.com/transaction.php?id=56874A dangerous hacker might attempt to replace the value 56874 for the id parameter with other comparable numbers, such as:
https://www.example.com/transaction.php?id=56875There is a possibility that the 56875 transactions are legitimate transactions belonging to somebody else. Web development companies should prevent from displaying this type of personal data in the transaction records of their clients.
IDOR vulnerabilities in case of password change form:
In most cases, “password change forms” are designed in a way that is vulnerable to IDOR attacks. For example, the URL for a poor password change form might look like this:
https://www.example.com/display_file.php?file.txt
There are file names in this URL. In these situations, the hacker makes use of IDOR vulnerabilities via directory traversal. The malicious hacker could gain access by changing the display_file.php script with /etc/passwd/file such as:
https://www.example.com/display_file.php?../../../etc/passwd
Defence Option:
The implementation of strict access control checks is the best strategy for protecting the website against IDOR vulnerabilities. You are fortunate to be able to create your website using frameworks like Ruby on Rails or Django, which strictly forbid easy access control. These methods of development are most widespread at Oplox Tech.
4-Sensitive Data exposure vulnerability in web security:

Any information that needs to be protected from unauthorized access is considered sensitive data, such as credit card information, credentials, or passwords. When a hacker accesses this type of information, he can uncover critical data that could cost the business millions of dollars.
Sensitive data will be in danger in two ways if a company’s website has weak security measures:
Data in Transit:
Data frequently moves via networks to other servers or via API. This data is extremely vulnerable if it is transmitted through an unsecured route. In these circumstances, any mechanism for data encryption, such as the SSL code layer, may have a weakness or small opening that allows data stealing to be done with ease.
Data at rest:
At rest, data on a website seems more secure, right? No, it is more vulnerable than data in motion. If the data being stored is not properly protected, attackers may employ various attack methods or malware such as Trojan horses or computer viruses. The best approach for attackers if the data is stored on a server is directory traversal.
Defence Options:
The data breaches are the result of inadequate website security. Give protecting credentials first attention while protecting website security by doing the things listed below.
- Use the proof-of-concept (POC) exploit to evaluate the website’s security. Compare the exploit with the vulnerabilities.
- Use the penetration test to evaluate the types of vulnerabilities that the website is exposed to. Applying this test throughout website development is preferred.
- Use several website security analysis tools, such as SAST and DAST. However, there are several drawbacks to these tools.
- Implement web application firewalls (WAFs). Although tough to maintain, it generates a lot of security alerts.
5-Missing function level access control vulnerability:
The missing function-level access control is the root of any website security vulnerability due to flaws in the authorization logic or a lack of permission checks for sensitive requests. The malevolent user, or even an existing user, can utilize corrupt requests to get access to restricted functionality. It all started with gaining access to API.
Access control vulnerability at the function level could be caused by URL manipulation. Suppose that the admin user of a website or web application is given the following URL.
example.com/account/remove
If any non-admin user or malicious attacker could acquire the /remove endpoint, this would be the missing control level failure.
Defence Option:
Protect your website from a vulnerability in function-level access control by using the following approach.
- Establish the website or application’s security policies.
- Review and update access control records using access control lists (ACLs).
- Make it mandatory to record and issue alerts for frequent authorization failures.
- At the business level, provide role-based access restrictions for code functions.
6-Cross Site Request Forgery vulnerability (CSRF):
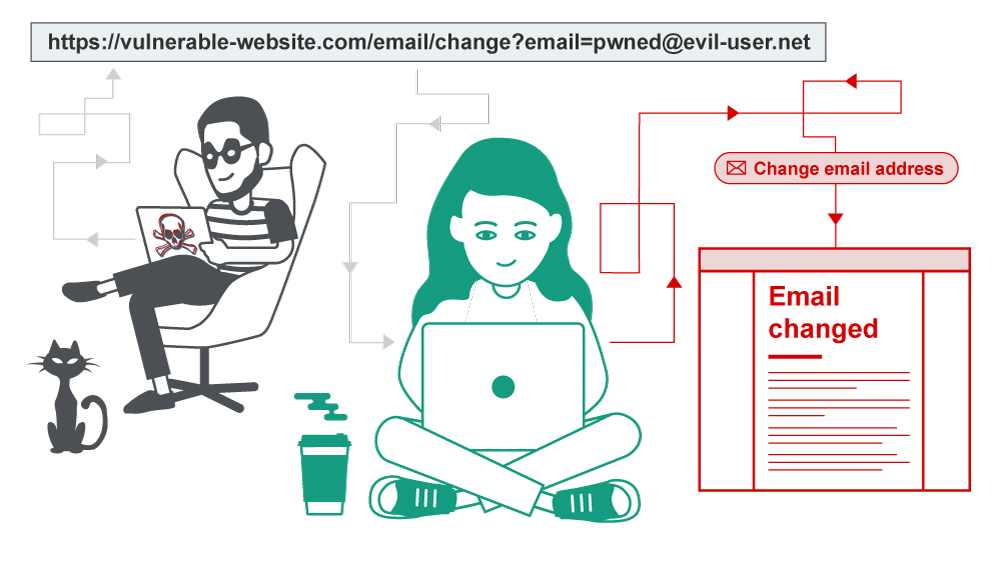
CSRF, or cross-site request forgery, is a web security flaw that lets an attacker trick users into doing things they didn’t mean to. It allows an attacker to partially bypass the same origin policy, which prevents distinct websites from meddling with each other.
In an efficient CSRF hack, the hacker induces the victim user to unwittingly do an action. For example, they may do this to alter their email address or login, or they could use it to send money.
Defence Option:
In order to prevent CSRF attacks, it is best to include a CSRF token in related requests. The token ought to be:
- Uncertain with high entropy.
- Connected to the user’s session ID.
- Rigorously verified in every situation before the required action is carried out.
7-Unvalidated redirects and forward vulnerability in web security:
The URL redirection vulnerability in a website makes the user’s request to go to an untrusted and malicious website where the user fills the login forms with their sensitive credentials. Although such sort of vulnerabilities don’t affect the website directly but harm the website’s reputation because such URL redirects are mostly used to orchestrate phishing scams and other social engineering attacks. Thus, the user data has been compromised successfully.
Defence Option:
- Avoid using URL redirection at all costs because it serves no benefit.
- Add an extra layer of security to URL parameters such as user ID, token, or response code mapping.
- It is best to employ IP filters and other server-side request forgery prevention measures when redirecting, as these may allow your app to evaluate whether or not the new URL is safe to use before redirecting the user.
Conclusion:
When it comes to protecting your website, establishing a partnership with a business that offers website security services in addition to website development might be a lifesaver. Although you can do the little things on your own, a professional should handle numerous security measures.
Oplox Tech offers security services by routinely checking your website for vulnerabilities, doing thorough website security audits, keeping an eye out for harmful behaviour, and being available for repair whenever necessary. These useful ideas cover the most important methods for securing your website; you and our staff must constantly exercise caution. Never stop looking for website security measures. Don’t let the villains win.


